Transcript
In February 2016, at Bangladesh Central Bank’s headquarters in Dhaka, something occurred that laid bare the profound weakness in the global financial system.
When banks move money around the world, they use a system called SWIFT – Society for Worldwide Interbank Financial Telecommunication – which is a consortium that operates a trusted and closed computer network for communication and payment orders between banks.
Today, SWIFT is used by over 11,000 financial institutions and more than 200 countries and territories. One of them is the Bangladesh Central Bank – BCB – with its headquarters in Dhaka, Bangladesh. On a daily basis, staff members at BCB would go into a highly secured room with closed-circuit security cameras, log into SWIFT and dispatch payment orders with encrypted communications.
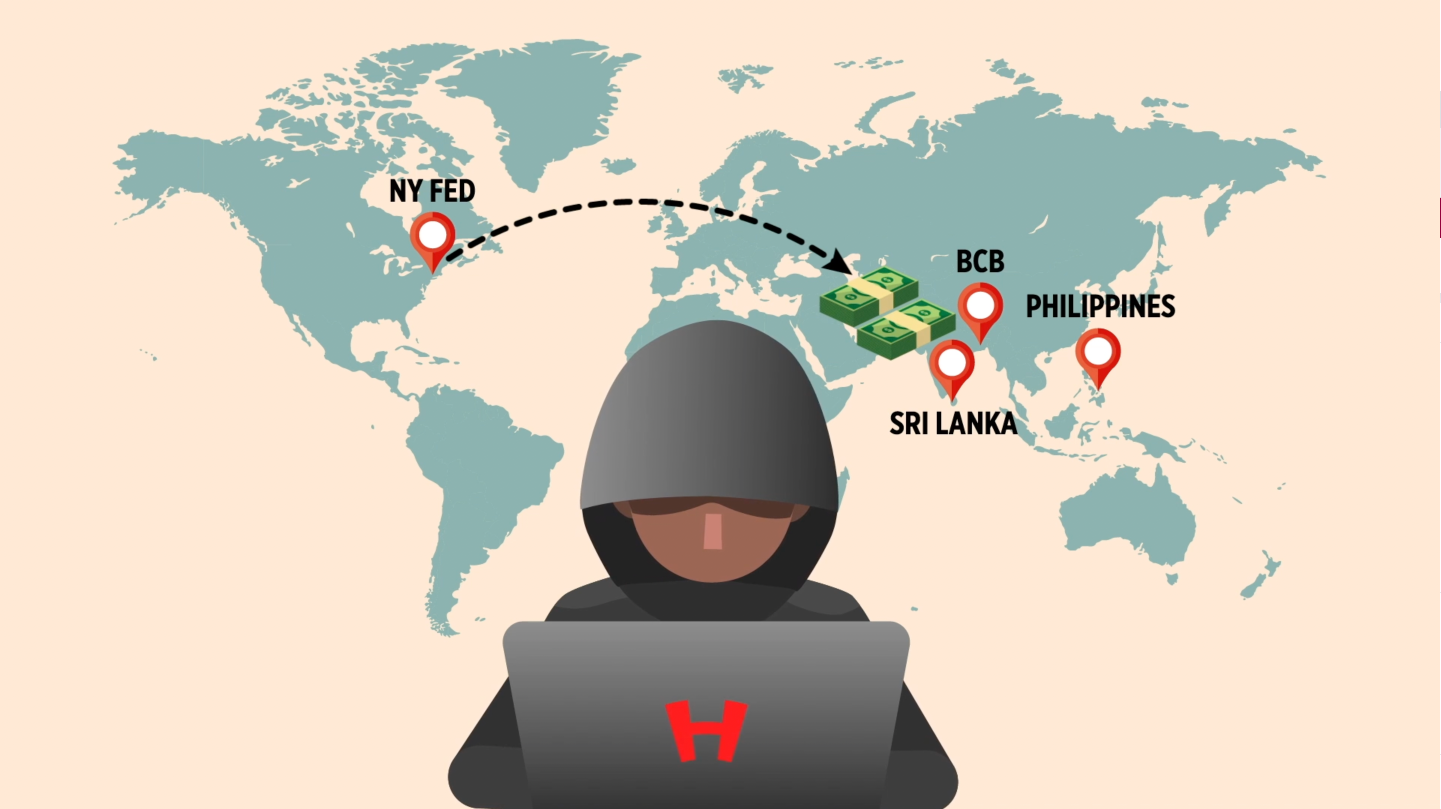
8000 miles away though, the New York Federal Reserve Bank is the gatekeeper of much of world banking, and hosts accounts for 250 central banks and governments – including the BCB. When the New York Fed receives a payment order, it follows the instructions and sends the money to the recipient. At the same time, it sends a confirmation letter back to BCB, marking the transaction completed. This process happens all around the world, every day, with about $5 trillion being directed via SWIFT. And the system is designed to be unbreachable.
On Thursday, February 4th, 2016, 35 payment orders using the credentials of the BCB’s employees were sent via SWIFT to the New York Fed. 5 of them went through, but the other 30 requests were blocked as the Fed system had detected a sensitive word in the recipient’s address and therefore flagged those transactions as suspicious. The next day, a total amount of $101 million was successfully transferred from BCB’s account to several accounts in Sri Lanka and the Philippines. But in the SWIFT operation room in Dhaka, it was quieter than usual. The printer was malfunctioning, so none of the confirmation letters got printed. They didn’t think much of it, assuming it was a small mistake, and were going to fix it the next day. After spending hours on Saturday getting the printers to work, the 35 payment requests caught the BCB employees by surprise, but the SWIFT communication system was still not working.
Assuming they were mistakes, the BCB employee tried to contact the New York Fed via email, phone and fax to cancel the transactions, but the Fed was shut down for the weekend. On the following Monday, BCB was able to get the SWIFT communications system working again. And it was not until then that they realized that the most daring bank robbery ever attempted using Swift had happened, four days ago. It would prove to be the most severe breach yet of a system designed to be unbreachable.
It turned out that the hackers had installed malware on BCB’s servers that had sent the 35 payment instructions and which deleted any incoming notices of the SWIFT confirmation messages. And, when the Fed was back in business that Monday, BCB was able to reach out and ask them to block the money transfer – but, it was too late and the money had already been sent to the recipient banks. So they sent SWIFT messages to the Philippines bank, RCBC, but it was a public holiday in the Philippines, so they would not be read until Tuesday, February 9th. And by that time, the money had already been transferred out.
Some funds were transferred to Sri Lanka and those funds were later recovered because of a misspelling of a word in the instructions, which triggered an alert at the local bank. But the 81 million USD that went to the Philippines was not. That money was sent to four fake accounts at a small Manilla branch of RCBC. From these accounts, the money was taken out and laundered through the Philippines casinos – never to be recovered. As the Philippines casinos in the country were not covered by anti-money laundering laws, it was a nearly impossible task to track the money. As of today, most of the money is still nowhere to be found.
Other similar cybercrimes have been reported elsewhere, such as in Vietnam and Ecuador, and other cases may come to light – and the hackers, however, have yet to be identified.
Discussion Questions
- The law usually takes time to react to technological change. How could it respond quicker or even stay ahead of the curve?
- How is technology making crime and illicit behaviour easier? How is it making it more difficult?
Additional Readings
- Zetter, K. (2016). That Insane, $81M Bangladesh Bank Heist? Here’s What We Know. Wired Magazine. Retrieved from https://www.wired.com/2016/05/insane-81m-bangladesh-bank-heist-heres-know/
- Hammer, J. (2018). The Billion-Dollar Bank Job. The New York Times. Retrieved from https://www.nytimes.com/interactive/2018/05/03/magazine/money-issue-bangladesh-billion-dollar-bank-heist.html
- Chernenko, E. (2018). Increasing International Cooperation in Cybersecurity and Adapting Cyber Norms. Council on Foreign Relations. Retrieved from https://www.cfr.org/report/increasing-international-cooperation-cybersecurity-and-adapting-cyber-norms
- Paul, R. (2018). Bangladesh to Sue Manilla Bank over $81-Million Heist. Reuters. Retrieved from https://www.reuters.com/article/us-cyber-heist-bangladesh/bangladesh-to-sue-manila-bank-over-81-million-heist-idUSKBN1FR1QV
- Lema, K. (2019). Philippine Court Orders Jail for Former Bank Manager over Bangladesh Central Bank Heist. Reuters. Retrieved from https://www.reuters.com/article/us-cyber-heist-philippines/philippine-court-orders-jail-for-former-bank-manager-over-bangladesh-central-bank-heist-idUSKCN1P40AG
- Segarra, L. M. (2017). The Guy From ‘Catch Me If You Can’ Says It’s Much Easier to Scam People Today. CNN. Retrieved from http://money.com/money/4953472/frank-abagnale-catch-me-if-you-can-scams-easier/
- Villasenor, J. (2016). Ensuring Cybersecurity In FinTech: Key Trends and Solutions. Forbes. Retrieved from https://www.forbes.com/sites/johnvillasenor/2016/08/25/ensuring-cybersecurity-in-fintech-key-trends-and-solutions/#7a65af1f35fd
- Frank Abagnale: “Catch Me If You Can” (2017). Talks at Google. Retrieved from https://www.youtube.com/watch?v=vsMydMDi3rI [VIDEO]